The biggest caution here is that when rundll32 fails, it may not notify https://dllkit.com/dll/libcef the user so the user may think the function is simply not working when in reality, rundll32 was supplied improper arguments. VersionStamper includes a number of sample conflict detection code templates that you can use to customize your own solutions. These approaches include displaying a warning to your users, or sending an Email message with detailed configuration information to a central help desk or technical support contact. You can even automatically download and install a correct set of files to your user’s computers.
- Tim Morgan wrote an excellent paper describing the structure of the Windows Registry, describing the various cell types and how they are interconnected.
- This hive is subclassed to both HKEY_CURRENT_USER\Software\Classes (user-specific settings) and HKEY_LOCAL_MACHINE\Software\Classes .
- I remember which I first got this machine, 3 days ago, I decided to not let it switch the screen around and answered lock when asked, but my Unlock does become active in Tent Mode.
If you want a complete look at what build is in which Insider channel, head over to Flight Hub. Please note, there will be a slight delay between when a build is flighted and when Flight Hub is updated. Due to an issue with migrating the shortcuts into the new Windows Tools location, This PC shows up with the display name “computer.” We already have a bug fix on the way to address this issue.
News On Uncomplicated Advice In Dll Files
The question is how to prevent this, and since users will have full access to their own machines, they have the ability to make these modifications. These are not "extremely insecure set of preconditions", this is very typical for any software being installed. Installation location will only prevent unauthorized users, not admins on the machine.
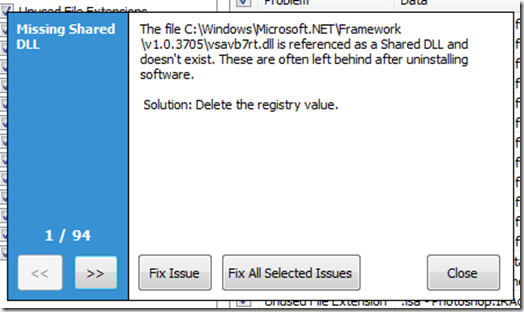
If Windows is whining about a missing or damaged file, you don't need to reload the system. That's a rather drastic measure, since you'd have to re-install all your software, as well as apply all the Windows Update security fixes.
Options For Speedy Systems Of Dll
For more details about the transaction log format, see this GitHub page. For a detailed description of the Windows registry hive format, see this research paper and this GitHub page. The Registry hives located in the Config folder of the Windows operating system can be opened using the built-in Registry Editor or any other third-party Registry Editing software.
Vital Criteria Of Dll Uncovered
However, if you know what you're doing, Resource Hacker is one way to do that. Another benefit of modularity is the use of generic interfaces for plug-ins. A single interface may be developed which allows old as well as new modules to be integrated seamlessly at run-time into pre-existing applications, without any modification to the application itself. This concept of dynamic extensibility is taken to the extreme with the Component Object Model, the underpinnings of ActiveX. When a program or software runs on Windows, much of how the application works depends on the DLL files of the program.